30+ data flow diagram threat model
It depicts external entities processes data stores and data flows. Once added they can be.
Bill Of Materials For Responsible Ai Collaborative Labeling Snorkel Ai
Use a data flow threat model analysis with the aid of intelligence tools to determine additional areas that are outside the boundary of common knowledge.

. Processes data stores and actors. Create threat models online. Some of the most valuable key.
Add model elements to your diagram by clicking or tapping the relevant shape in the stencil on the left side of the diagram editor. The resulting document is the threat model for the application. This white paper looks at some flaws and the advantages of moving to a more mature Process Flow Diagram PFD approach to threat modeling as a solution.
In the diagram an. User Login Data Flow Diagram for the College Library Website. Threat modeling analyzes how an adversary might attack a system by supplying it with malicious data or interacting with it.
Use data flow diagrams for a profound understanding of your application Now that you know more about the why and how of threat modeling it is time to take a deeper look into the data. Visual Paradigm Online features an online threat model maker and a large variety of technical and. Threat modeling is a structured approach of identifying and prioritizing potential threats to a system and determining the value that potential mitigations would have in reducing or.
The numbers represent data flows where the data moves across a trust boundary. We start by deciding to focus on either what needs to be protected or who it. The analysis uses a Data Flow Diagram DFD to describe how data.
A threat model diagram is a visual form of threat model. We extended Reexion Models to check the. Threat modeling is a lightweight approach to reason about application security and uses Data Flow Diagrams DFDs with security annotations.
Everything outside the web server boundary is assumed to be the internet. A Data Flow Diagram DFD as the name indicates shows the flow of data through the system. Microsofts Threat Modelling Tool This tool identifies threats based on STRIDE threat model classification and is based on Data Flow Diagram DFD which can be used to.
Threat modeling is an effective technique to help you identify threats and ways to reduce or eliminate risk.
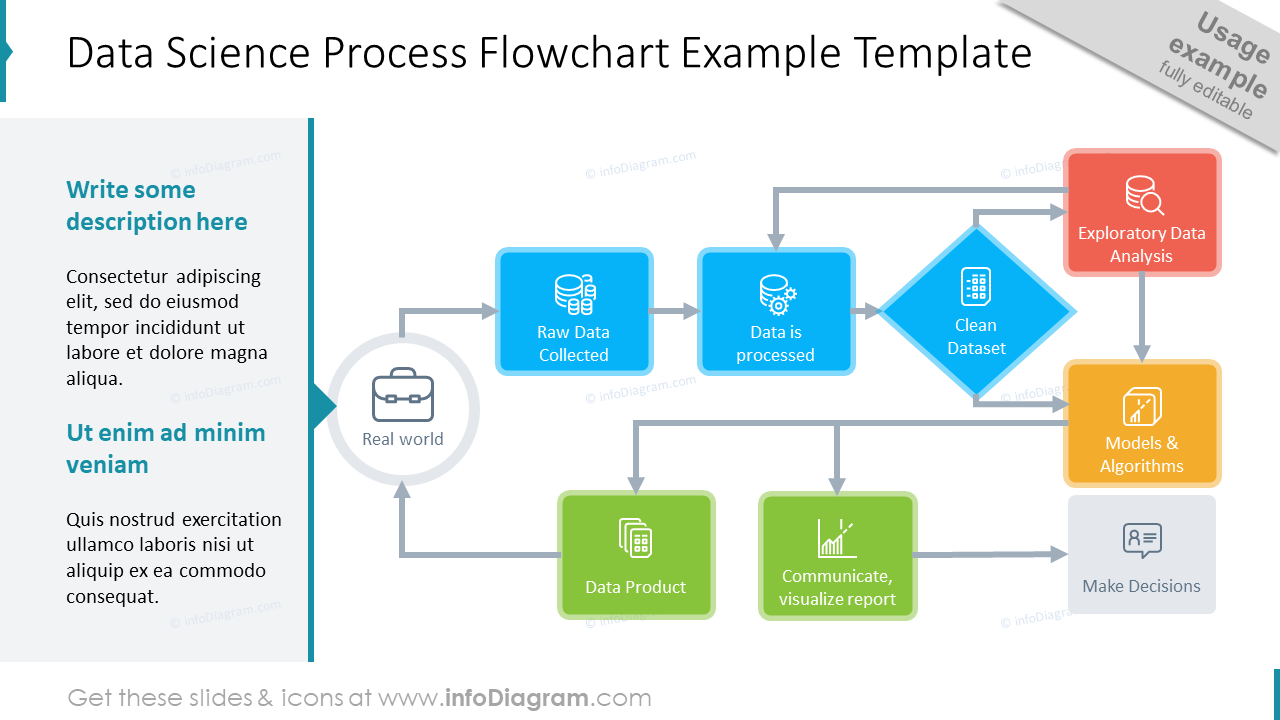
30 Data Science Line Icons Of Big Data Predictive Analytics Definitions Processes As Powerpoint Presentation Infographics
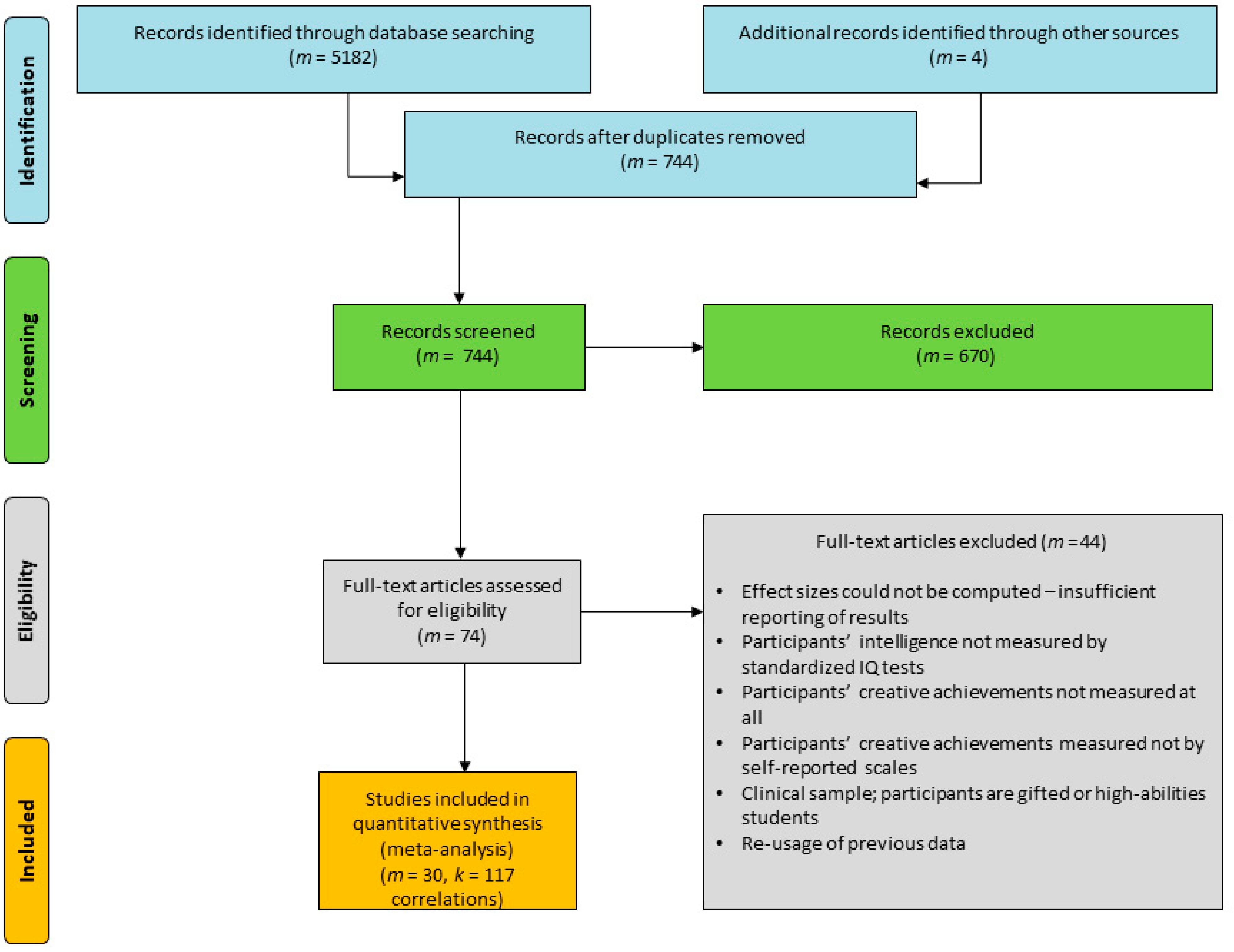
J Intell Free Full Text How Is Intelligence Test Performance Associated With Creative Achievement A Meta Analysis Html

Next Generation Security Operations With Aws
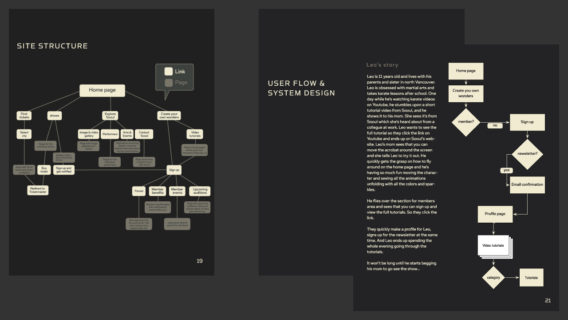
How To Design A User Flow Diagram For Your Website
What Is Erd And Dfd Quora

A Threshold Based Real Time Analysis In Early Detection Of Endpoint Anomalies Using Siem Expertise Sciencedirect

Next Generation Security Operations With Aws
What Is The Purpose Of Developing Dfds Quora

Bill Of Materials Bom As A Foundation For Plm Erp Mes Integration Prostep Us
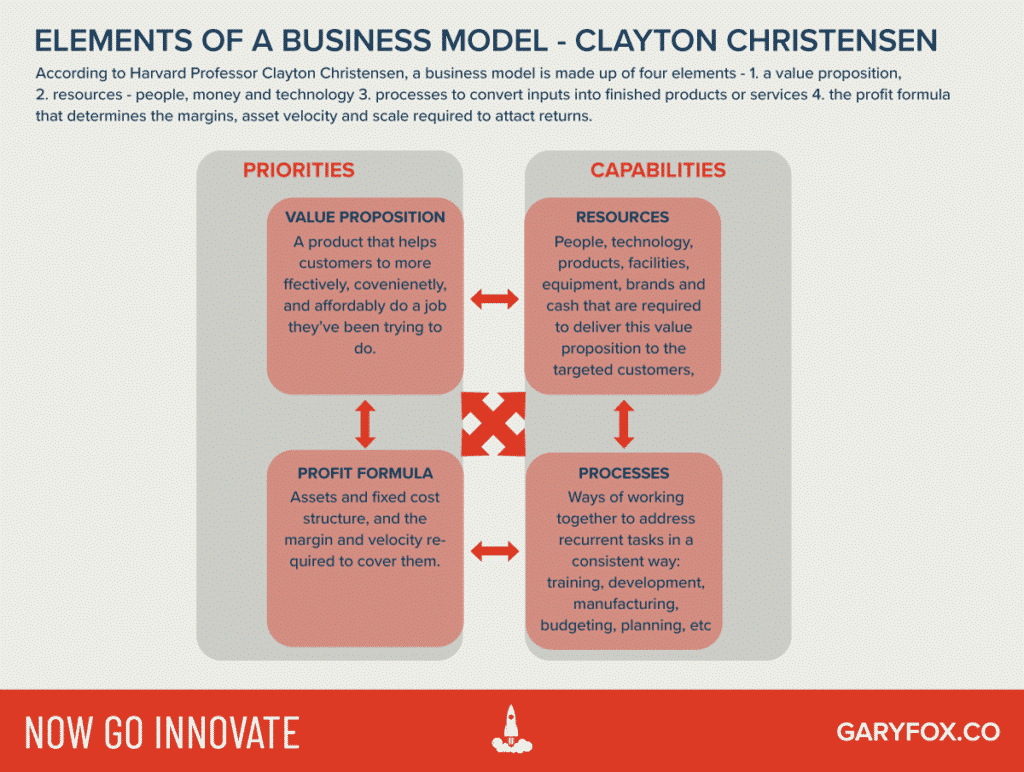
What Is A Business Model Definition Explanation 30 Examples
![]()
Threatmodeler About The Evolution Of Threat Modeling
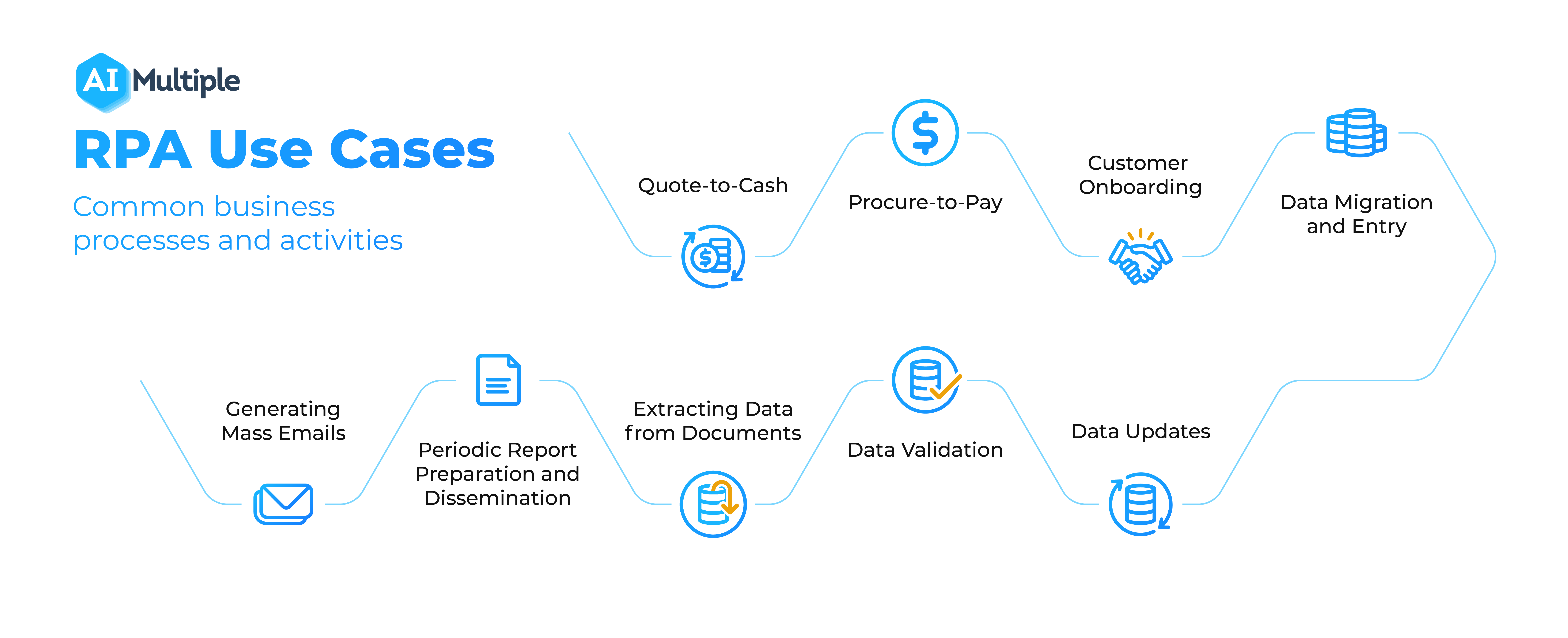
Top 65 Rpa Use Cases Projects Applications Examples In 2022

Real Time Operational Monitoring Of Renewable Energy Assets With Aws Iot Aws For Industries
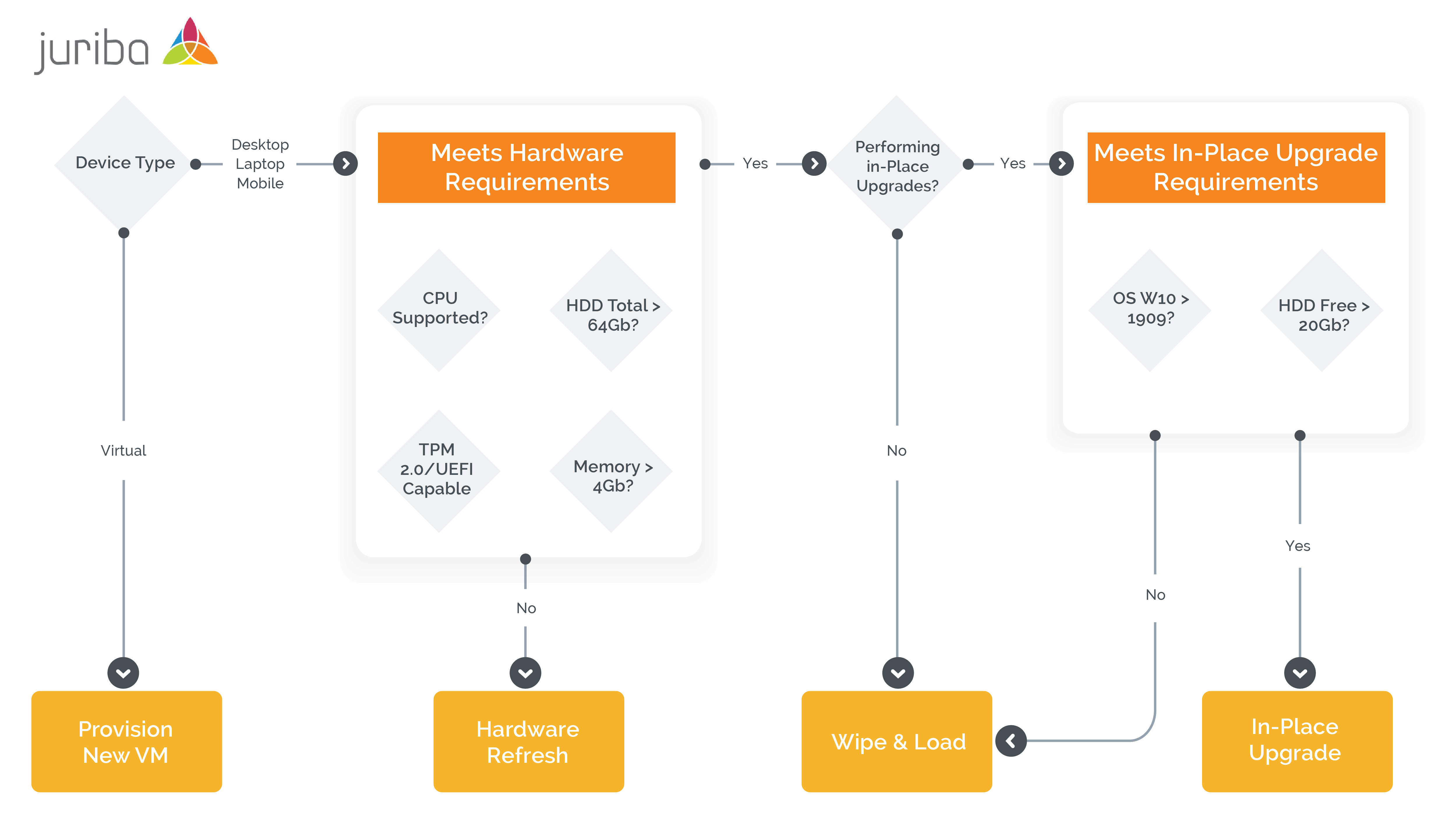
In Place Wipe Load Or Hardware Refresh How Windows 11 Hardware Requirements Will Determine Your Migration Strategy
100 Ai Use Cases Applications In 2022 In Depth Guide

Study Flow Diagram Ipd Individual Participant Data Lns Lipid Based Download Scientific Diagram
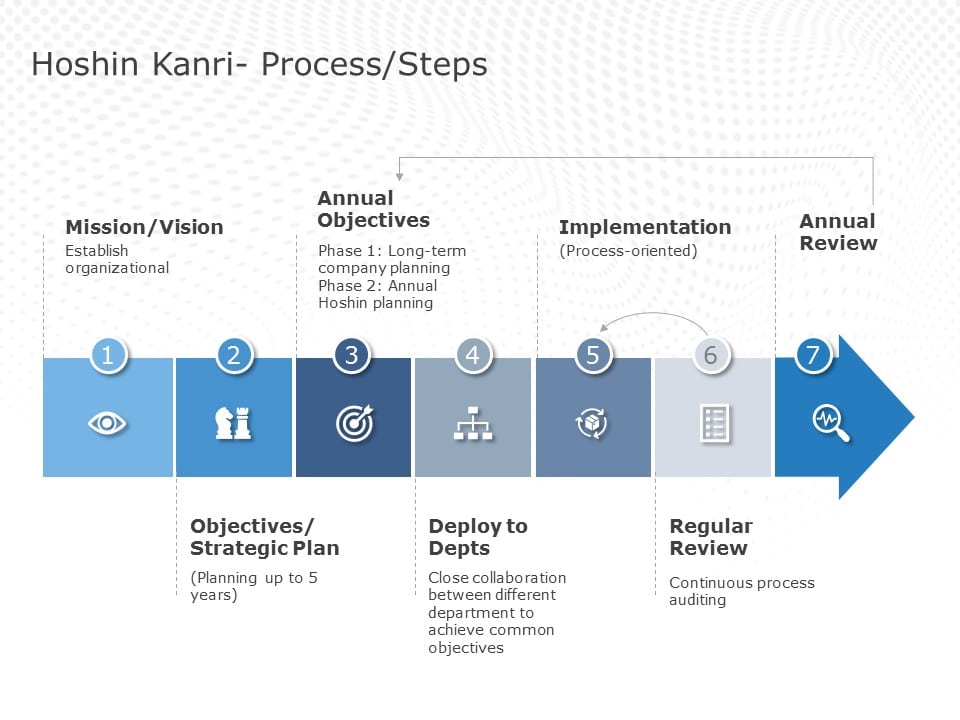
1567 Editable Free Flow Chart Templates Slides For Powerpoint Presentations Slideuplift